Don't just defend, anticipate.
Experience the power of proactive protection.
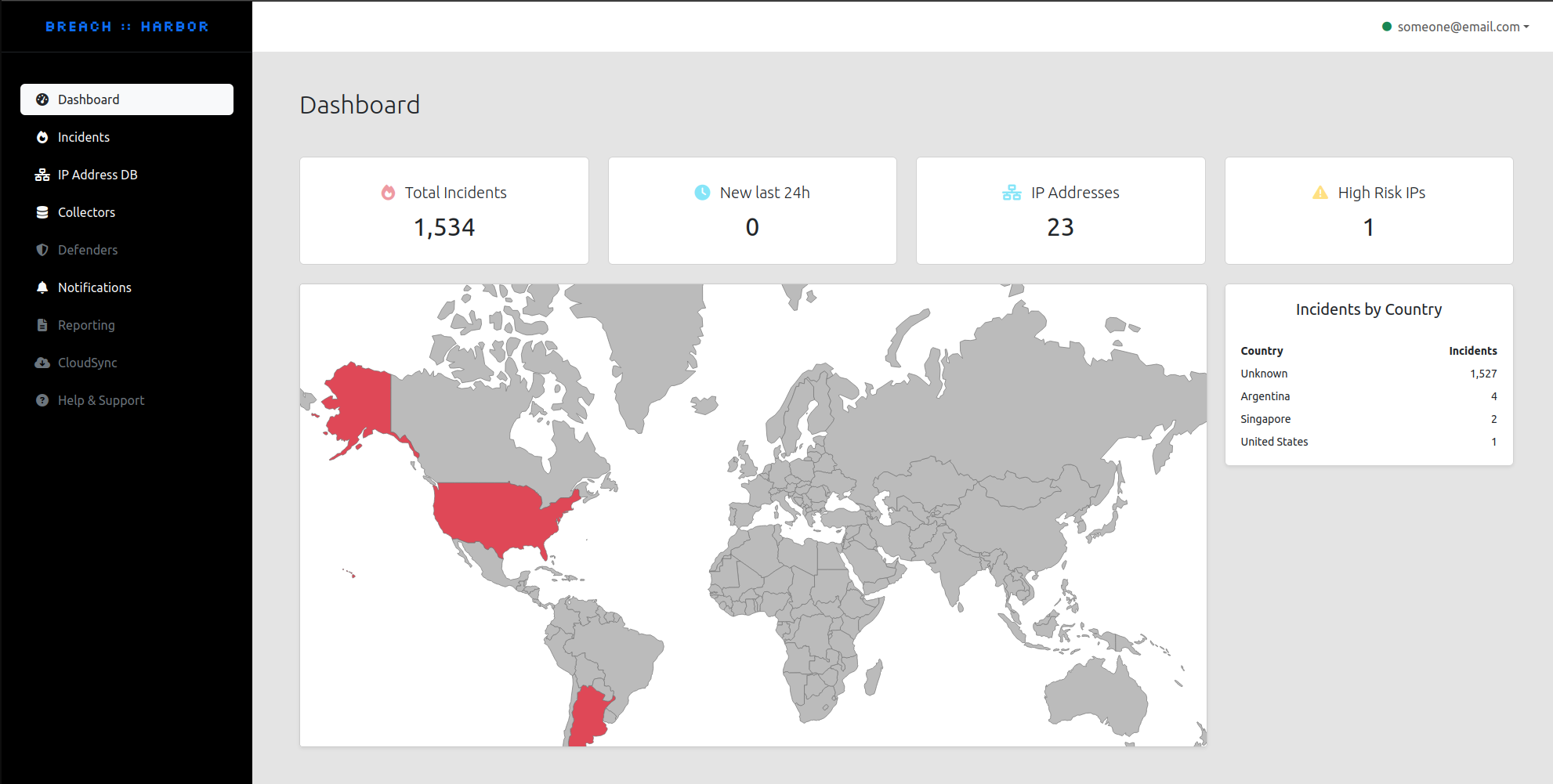

BREACH::HARBOR is a state-of-the-art cybersecurity suite designed to safeguard digital assets against both existing and emergent cyber threats. By leveraging a combination of local data collection and global threat intelligence, this platform offers an unparalleled, proactive defense mechanism.
This project is in its early stages and is not yet recommended for production use.
Identify and analyze potential threats as they emerge with comprehensive monitoring.
Deploy collectors across multiple network environments for comprehensive coverage.
Leverage global threat data to enhance local security posture and response.
Intuitive dashboard for threat monitoring and analysis of security incidents.
Configure customized security policies and automated threat responses.
Stay ahead of threats with predictive intelligence and early warning systems.
BREACH::HARBOR is elegantly streamlined into three primary components:
Central hub where data is processed, analyzed, and visualized for interpretation.
Enforces robust security policies based on intelligence from the Core API.
flowchart LR
User([User Environment]) --> Collector
subgraph Components [" "]
direction LR
Collector[COLLECTOR]
CoreAPI[CORE API]
Defender[DEFENDER]
Collector --> |Threat Data| CoreAPI
CoreAPI --> |Security Policies| Defender
Defender --> |Protection| User
end
style Components fill:none,stroke:none
style Collector fill:#1e1e1e,stroke:#555,color:#f8f9fa,stroke-width:1px
style CoreAPI fill:#1e1e1e,stroke:#007bff,color:#f8f9fa,stroke-width:2px
style Defender fill:#1e1e1e,stroke:#555,color:#f8f9fa,stroke-width:1px
style User fill:#1e1e1e,stroke:#555,color:#f8f9fa,stroke-width:1px,stroke-dasharray: 5 2
Enhance your security with commercial threat intelligence data
CloudSync is our upcoming premium service that will provide real-time commercial threat intelligence feeds to enhance your security posture. Stay ahead of emerging threats with curated data from our global security research team.
For now, only development/local setup is supported.
git clone https://github.com/Dyneteq/Breach-Harbor-Core-API.git
cd Breach-Harbor-Core-API
cd breach_harbor_core
python -m venv .venv
source .venv/bin/activate
pip install -r requirements.txt
python manage.py migrate
python manage.py runserver 0.0.0.0:8000
cd client
npm install
npm run start